An OSCP journey without using METASPLOIT — HTB Nibbles#2
So yesterday begun the jouney to OSCP 2020 during Covid 19. I completed Bashed a Linux based Easy box. Todays challanges “Nibbles”

Things we already know:
Rating: Easy | Operating system: Linux | IP: 10.10.10.75
Recon


HTTP Enum:
As always when we see port 80(HTTP) or 443 (HTTPS) open we look for low hanging fruit with Nikto and Gobuster.


With not much to go off here the next logical step is Right click view source

We identify “/nibblelog/ and the word directory lets navigate there.

Usually the first thing I look for is places for user input (things like search field and contact us pages) in this sense thats not possible. We see Powered by Nibbleblog….. whats that???

When in doubt …… consult the ORACLE!

Ok so open source blogging software that uses PHP. Having access to the software can be an extremely valuble technique in pentesting as offline means no detection. We can download the software and understand how the application is configured to look for vulnerabilities furthermore open source means,people that have used it historically may of reported vulnerabilities.
I went to the Githubpage by dignajar. This is usually a great place for further information. Im particular intrested in identifying the version of nibbleblog that is running from here I can see if there is publicly available exploits to leverage.

This is Golden each one of these “.php” is usuall a directory bolted on to the applicaiton I headed straight for “admin.php”

Still no version though! I checked in the “view source” but no luck.


After going through the entire list from github it happend to the last one I tried “update.php” which revealed “Nibbleblog version 4.0.3”
If the Github page provided no results for version enumeration we could of achieved the same resutls using “Gobuster”



I copied the highlighted text and googled it as I like to to use the Rapid 7 websites where possible.

Nibbleblog contains a flaw that allows an authenticated remote attacker to execute arbitrary PHP code. This module was tested on version 4.0.3.
In a real pentest I would go ahead and use metasploit module as why not thats what its there for however that wouldnt be much fun and this is meant to be OSCP practice therefore we need to limit the use of metasploit as much as possible.

A bit of googling around I came to this page https://packetstormsecurity.com/files/133425/NibbleBlog-4.0.3-Shell-Upload.html on this page gives us more infomration on how this file upload vulnerability works
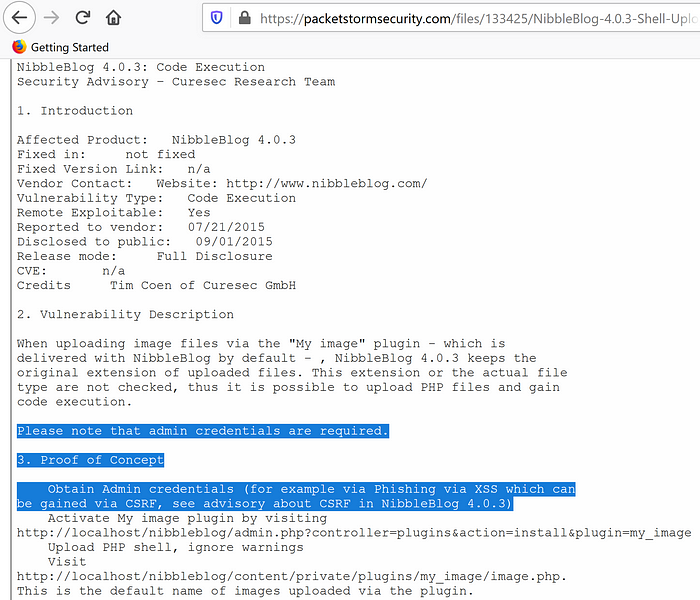
From this description we understand that when exploited this will allow code execution. However we need admin credentials. The vulnerability is in the “My image” plugin that allows the upload of PHP files. So it would allow us to upload a PHP reverse shell from our webshells directory. Read my last post for further info on this.

Ok so at this moment I sat back in my chair and thought is this a rabbit a hole is this the way in ? I went back to my nmap results, only one port open however I did only do an intial default scan of the top 1000 TCP ports, I begun to run a all port scan in the background.
I had some intial options whilst waiting for the nmap results.
- Bruteforce the login form (does account lock out exsit?)
- Fuzz the domain more
- Identify default credentials.
Firstly I decided to understand how the “admin login” area worked. I span up Wireshark and attempted to login with the credential batman:superman, I captured this in Wireshark and viewed the results

For application/x-www-form-urlencoded, the body of the HTTP message sent to the server is essentially one giant query string -- name/value pairs are separated by the ampersand (&), and names are separated from values by the equals symbol (=). An example of this would be: username=batman&password=superman
When you post the form, the payload for x-www-form-urlencoded note how strings are encodeURIComponent()

I clicked on the “Forgot Password” tab to identify how the functionality works.
My next plan is run Hydra or Medusa in the background for this we will need the “http-post-form”

I made a very small username list and used rockyou wordlist located in the /usr/share/wordlists directory.

I ran Hydra in an attempt to bruteforce the password and left it running most of the day, I came back a couple hours to view the results and guess what !!! NOTHING !!! I was literally out of options this is a easy ranked box ( got me sweating now) I even tried CeWL

No luck there though. At this point I had messaged my friend whos ranked Guru on HTB, he only started about a year ago an absolute ninja although he dosnt see it, he said he hasnt done nibbles but is will start it at lunch, well this was even worse !! Not only had I exhausted all options I could think of to gain access to the admin portal, Javier was hot on my toes I could let him start after me and root it before me!!
Here a link to a BASH script that will attempt HTTP Brute Force with account lockout in mind If it gets locked, it waits 60secs and then continues. The X-Forwarded-for header is there to make the target believe the HTTP requests are coming from different IPs (effectively disguising us as a proxy), therefore delaying the lockoutCheck out the company I work for Github page as I go through the PWK 2020 and build up my own collection of tools and scripts.
https://github.com/CYSIAM/Offensive-Juice/blob/master/HTTP-auth-brute.shI had no option I navigated to to the HTB forum page and located the “Nibbles” section. I knew others would be having the same issue as me after all I have followed everything in the standard methodology, right? After about 25 mins flicking through I came to a comment “ The password is right infront of you” intially didnt give me much more information, then I tried the box name “nibbles” low and beyond after about a total of 9hrs searching for this password it was bloody “nibbles” turns out I had missed the oldest trick in the book! Note to oneself, remember to try OBVIOUS passwords. Finally I had access to the portal just like the exploit proof of concept told us I navigated to the images section under Plugins.

I upload my php-reverse-shell.php and set my listner, to initiate the conection navigate to “http://10.10.10.75/nibbleblog/content/private/plugins/my_image/image.php”


I typed [which python] to see if Python was present on the box it wasnt so tried [which python3] and got a positive response. This gave me a more interactive shell. From here my aim is to enumerate further to find information we can use to elevate my privellage to root. Just as the PWK mannual suggests, we restart our enumeration once we have shell looking for services,processes,configs etc this info will be used to elevate from user “nibbler” to “root”



I attempted to view the contents of the scripts.
cat home/nibbler/personal/stuff/monitor.shBut I got the response “No such file or directory” …. hmm ?! It dosnt exist. I created the following:
mkdir -p home/nibbler/personal/stuff
cd /home/nibbler/personal/stuffThen used “echo [/bin/bash” > monitor.sh]
Chmod 777 monitor.shThe above gives all three, Owner | Group | everyone else RWX permissions
sudo /home/nibbler/personal/stuff/monitor.shFinally rooted ! With a bit of help from a friend and the forums thats number 2 rooted from TJ nulls list.
Lessons learnt for OSCP
- Nibbleblog version 4.0.3 is vulnerble to file upload. If the application software is open source, check github and use the /index or/update page to enermerate application version. For fileupload should my .php extension not of worked due to file upload restrictions I would of attempted to bypass by adding a null byte injection (shell.php%00.gif) or by usingdouble extensionsfor the uploaded file like ( shell.jpg.php).
- For restrictred shell search what language is present on the target using the [which python] command as an example. then use the [python3 -c ‘import pty; pty.spawn(“/bin/bash”)’] command.
- When attempting login bypass remember to use ovbious names “nibbles” for a box called “nibbles” what an idiot still gets me!
Remediations
- Ensure that sensitive information is removed from banners, such as the Apache version number we was able to enumerate using telnet as per A3 of the OWASP top 10, see here for futher info. https://owasp.org/www-project-top-ten/OWASP_Top_Ten_2017/Top_10-2017_A3-Sensitive_Data_Exposure
- Ensure weak credentials are not used, consider using passphrases or the use of password managers see here for more info https://www.ncsc.gov.uk/collection/passwords
- Using components with known vulnerbilties as per A7 OWASP top 10, Nibbleblog has a known remote code execution vulnerbility and is also end of life therefore not supported. Upgrade this applicaiton to newer Blog software
- Ensure that least privellege model is followed that users cant run scripts as root.
Thats box number 2 down and rooted. Tune in once again for my jouney to OSCP 2020 without using metasploit during the COVID 19 pandemic thanks for reading all!
